Subscribe to our Newsletter
Elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Latest News
Healthcare Ransomware Case Study 2025
Anatomy, Impact & NIST CSF DefenseCase Study: Responding to a Healthcare Ransomware Attack Introduction: When…
Service Mesh vs API Gateway: Security Implications
Security should move at the speed of your pipeline. As organizations modernize with Kubernetes and…
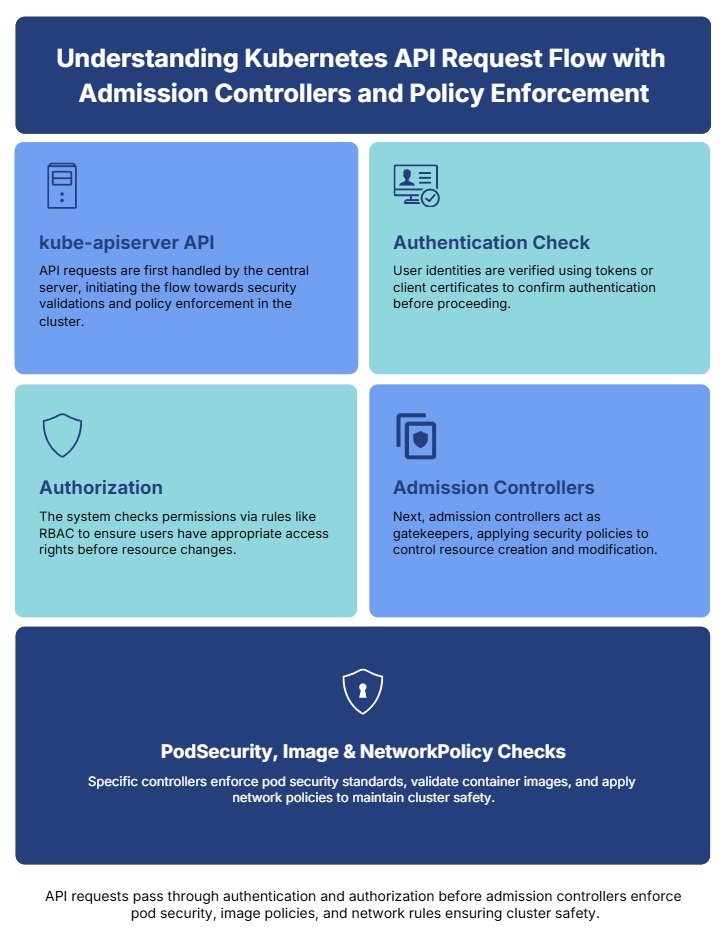
Kubernetes Admission Controllers: Security Use Cases – Complete Guide
Security should move at the speed of your pipeline. When teams scale to multiple clusters,…
Container Supply Chain Security: Image Signing and Verification
In the modern CI/CD pipeline, the container is the new currency of deployment. But just…
Serverless Functions Security: AWS Lambda, Azure Functions, GCP Cloud Functions
Securing Serverless Functions Security should move at the speed of your pipeline. Serverless computing accelerates…
Multi-Tenant Kubernetes Security Challenges
When teams scale to multiple clusters, visibility gaps grow fast. Kubernetes was designed for flexible…