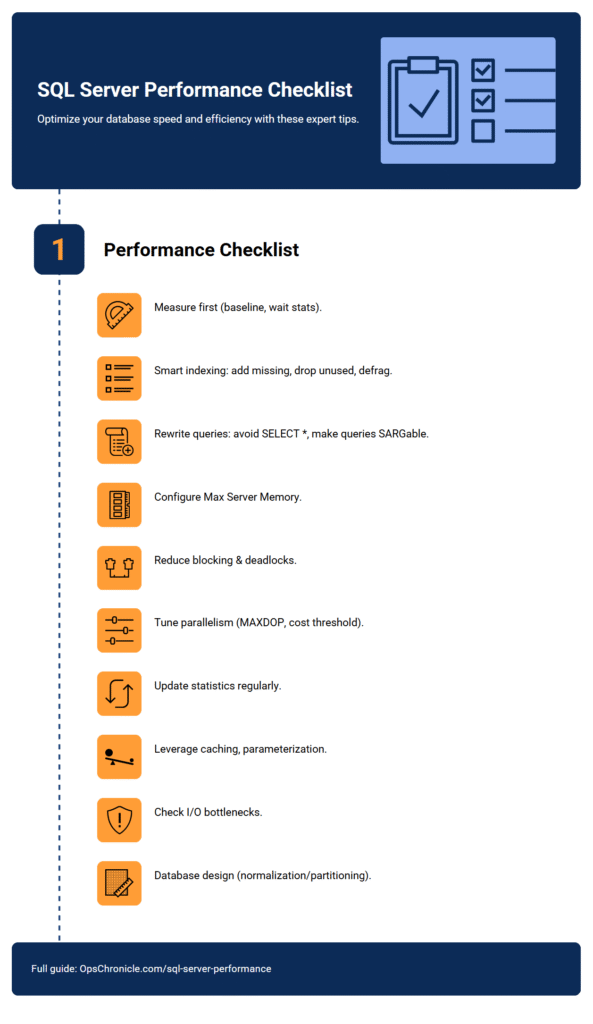
Security should move at the speed of your pipeline. As organizations modernize with Kubernetes and microservices, two key components often appear in the architecture: the API gateway and the service mesh. Both handle communication, but their security responsibilities differ. Understanding where each control fits prevents gaps in protection and avoids overlapping complexity.
What Is an API Gateway?
An API gateway is the single entry point for external clients into your microservices environment. It acts as a front door that routes, authenticates, and secures requests before they reach backend services.
Key Security Functions of an API Gateway
- Authentication & Authorization: Validates tokens (JWT, OAuth2) before forwarding requests.
- Rate Limiting & Throttling: Protects APIs against abuse or DoS attempts.
- TLS Termination: Ensures encrypted transport from clients to gateway.
- Input Validation: Filters malformed or malicious requests.
In practice: API gateways secure the north–south traffic — everything that flows between external consumers and your system.
What Is a Service Mesh?
A service mesh manages service-to-service communication inside your cluster. Typically implemented with sidecar proxies (e.g., Envoy in Istio or Linkerd), it enforces policies transparently without changing application code.
Key Security Functions of a Service Mesh
- mTLS Encryption: Automates certificate management and enforces encrypted service-to-service communication.
- Service Identity & Policy: Provides workload-level identity (SPIFFE/SPIRE) and applies authorization policies.
- Zero Trust Principles: Ensures “never trust, always verify” across microservices.
- Observability with Security Context: Logs and traces can detect lateral movement attempts.
In practice: Service meshes cover the east–west traffic — communication within the cluster.
Service Mesh vs API Gateway: Security Comparison
| Security Dimension | API Gateway (North–South) | Service Mesh (East–West) |
|---|---|---|
| Traffic scope | Client-to-service | Service-to-service |
| Identity & auth | OAuth2, JWT validation at edge | Workload identity, certificate rotation, service policies |
| Encryption | TLS termination | Automatic mTLS between pods |
| Rate limiting | Yes — protects external APIs | Limited — not its primary purpose |
| Threat visibility | API usage monitoring, WAF rules | Distributed tracing, anomaly detection inside cluster |
| Compliance impact | Demonstrates secure API exposure (PCI DSS, GDPR) | Supports Zero Trust and defense-in-depth requirements |
Security Risks of Misuse
- Relying only on API Gateway: Leaves east–west traffic unencrypted, exposing sensitive data inside the cluster.
- Relying only on Service Mesh: Secures internal calls, but APIs remain exposed without strong external auth controls.
- Duplicated Policies: Teams sometimes configure TLS and auth in both layers inconsistently, creating drift.
Best Practices for Secure Architectures
- Use Both, But with Clear Roles
- Gateway secures external access.
- Mesh secures internal microservice traffic.
- Integrate with Identity Providers (IdPs)
- Delegate API gateway authentication to IdPs (Okta, Azure AD).
- Use SPIFFE/SPIRE or mesh-native identity for workloads.
- Apply Zero Trust Principles
- Enforce least privilege access between services.
- Continuously verify identities and rotate certs.
- Centralize Policy Management
- Align gateway and mesh policies to avoid conflicting rules.
- Use GitOps or IaC pipelines for version-controlled policies.
- Measure & Monitor
- Collect metrics from both layers into your SIEM/SOC.
- Detect anomalies such as unusual API call rates or lateral movement.
When to Prioritize One Over the Other
- Start with API Gateway if your main challenge is exposing secure APIs to partners, mobile apps, or external systems.
- Add Service Mesh as microservices scale and internal security gaps emerge (especially in regulated industries).
- Enterprise environments often require both, integrated into a multi-layered security blueprint.
Conclusion
API gateways and service meshes are complementary security layers. One protects the edge, the other the interior. When aligned, they form guardrails that support compliance, resilience, and Zero Trust adoption in cloud-native systems.
Embed controls early and measure continuously. That’s how you balance speed, scale, and security in modern architectures.
FAQ: Service Mesh vs API Gateway Security
What is the main security role of an API gateway?
To authenticate, authorize, and protect traffic entering the cluster from external clients.
How does a service mesh improve security?
By enforcing mTLS, workload identity, and fine-grained policies on service-to-service communication.
Do I need both service mesh and API gateway?
Yes, in most cases. API gateways secure north–south traffic, while service meshes secure east–west communication.
Which should I implement first?
Start with an API gateway to secure external exposure. Add a service mesh as microservices grow and internal security becomes critical.
No post found!