Service Mesh vs API Gateway: Security Implications
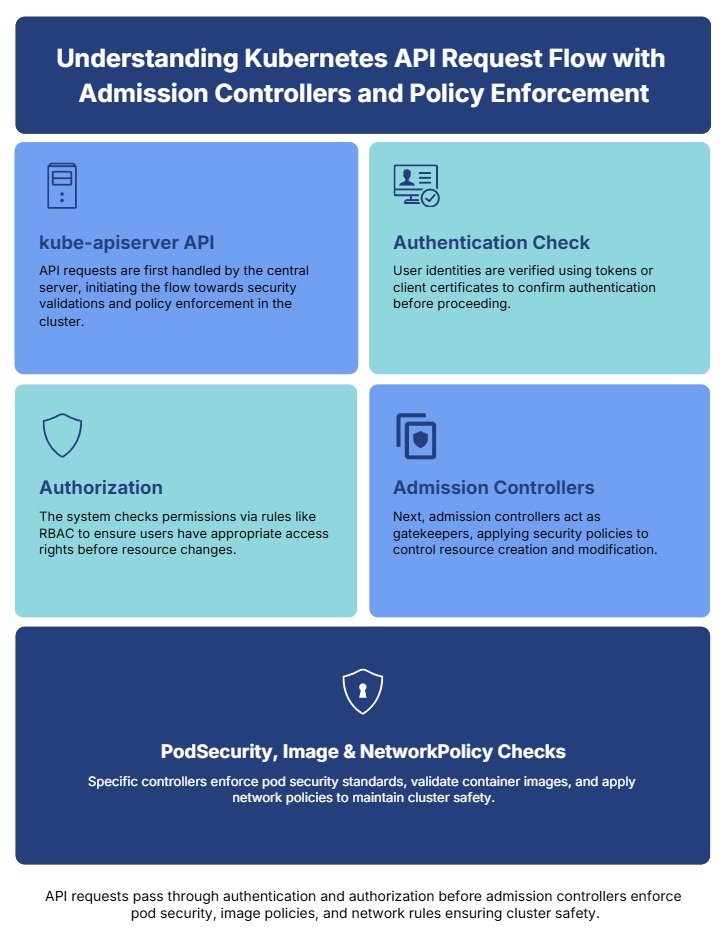
Security should move at the speed of your pipeline. As organizations modernize with Kubernetes and microservices, two key components often appear in the architecture: the API gateway and the service mesh. Both handle communication, but their security responsibilities differ. Understanding where each control fits prevents gaps in protection and avoids overlapping complexity. What Is an […]
Service Mesh vs API Gateway: Security Implications Read More »