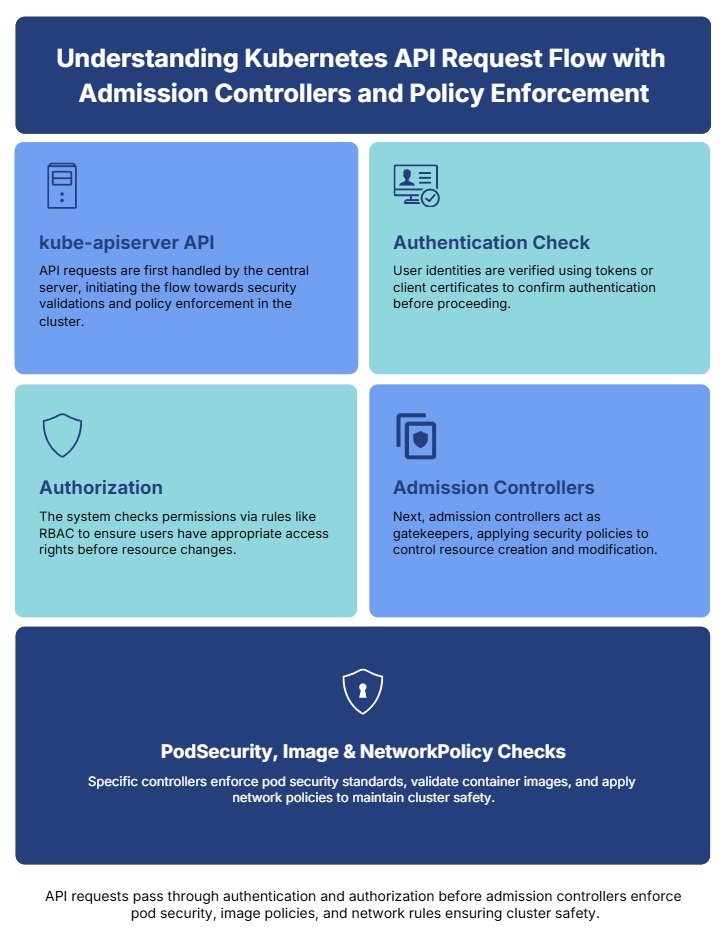
Security should move at the speed of your pipeline. When teams scale to multiple clusters, visibility gaps grow fast — so embedding preventive controls directly into your Kubernetes API layer becomes critical. In practice, admission controllers serve as security gatekeepers that intercept API requests before persistence, enabling policy enforcement, validation, and mutation of resources.
As a Cloud & DevSecOps Specialist with over a decade securing enterprise environments, I’ve implemented admission controllers across global fintech and healthcare Kubernetes deployments. Therefore, this guide focuses on practical security use cases you can implement today, not just theoretical concepts.
What Are Kubernetes Admission Controllers?
Kubernetes admission controllers are plugins that govern operations on the Kubernetes API server. They act as strategic choke points for enforcing security policies and operational best practices — essentially serving as built-in guardrails for your cluster operations.
Admission controllers execute in two phases:
- Validating admission controllers — Verify whether requests should be permitted (without modification)
- Mutating admission controllers — Modify requests before processing to apply defaults or transformations
In practice, most security implementations leverage both types to create layered defenses. For example, you might mutate pods to inject sidecar proxies while validating that deployments don’t mount sensitive host paths.
Critical Security Use Cases for Admission Controllers
1. Enforce Pod Security Standards
The PodSecurity admission controller (replacing PodSecurityPolicies in v1.25+) enables enforcement of the Kubernetes Pod Security Standards. This represents your first line of defense against privileged containers.
Implementation example:
yaml
apiVersion: apiserver.config.k8s.io/v1
kind: AdmissionConfiguration
plugins:
- name: PodSecurity
configuration:
defaults:
enforce: "restricted"
enforce-version: "latest"
exemptions:
usernames: ["system:serviceaccount:kube-system:privileged"]
So why does this matter? According to the 2024 Cloud Native Security Report, 56% of organizations experienced container runtime incidents — with privileged containers being the primary attack vector. Therefore, implementing Pod Security Standards significantly reduces your attack surface.
2. Prevent Overprivileged Containers
Validating admission controllers can enforce security policies that prevent:
- Containers running as root
- Privilege escalation capabilities
- Host namespace sharing
- HostPath volume mounts
Here’s a practical OPA Gatekeeper constraint template that prevents privileged containers:
yaml
apiVersion: templates.gatekeeper.sh/v1beta1
kind: ConstraintTemplate
metadata:
name: k8sblockprivileged
spec:
crd:
spec:
names:
kind: K8sBlockPrivileged
targets:
- target: admission.k8s.gatekeeper.sh
rego: |
package k8sblockprivileged
violation[{"msg": msg}] {
containers = input.review.object.spec.template.spec.containers
c_name := containers[_].name
containers[_].securityContext.privileged
msg := sprintf("Privileged mode is not allowed for container %q", [c_name])
}
3. Implement Image Registry Whitelisting
Image policy admission controllers restrict which registries can deploy containers — a fundamental zero trust practice for container security. This prevents unauthorized images from unknown registries from entering your environment.
Key validation checks should include:
- Registry domain whitelisting
- Image signature verification
- Vulnerability scan status requirements
- Image age restrictions (prevent stale base images)
As a result, teams eliminate “shadow IT” containers while ensuring all deployed images meet organizational security standards.
4. Validate Network Policies
Admission controllers can validate NetworkPolicy resources to ensure they meet organizational standards before application. This prevents overly permissive network policies that might expose sensitive workloads.
Common validation rules include:
- Requiring default-deny policies in all namespaces
- Preventing policies that allow 0.0.0.0/0 ingress
- Ensuring production namespaces have explicit ingress/egress rules
- Validating that policies don’t conflict with mesh layer security
5. Inject Sidecar Containers Securely
Mutating admission controllers automatically inject sidecar containers like service meshes, security agents, or logging components. This ensures consistent security posture across all deployed workloads without relying on developer implementation.
For example, the Istio sidecar injector uses a mutating admission webhook to automatically add Envoy proxies to pods in labeled namespaces. Similar patterns work for security monitoring agents and logging sidecars.
Implementation Strategy: Gradual Enforcement
When implementing admission controllers, follow a phased approach:
- Audit mode — Log violations without blocking operations (measure drift)
- Warn mode — Return warning messages to API clients while allowing requests
- Enforce mode — Reject non-compliant requests (after addressing false positives)
This graduated rollout prevents operational disruption while giving teams time to adapt their deployments to meet security requirements.
Comparing Admission Controller Solutions
| Solution | Type | Learning Curve | Cloud Provider Support |
|---|---|---|---|
| OPA/Gatekeeper | Validating Webhook | Moderate | AWS EKS, Azure AKS, GCP GKE |
| Kyverno | Both Validating & Mutating | Low | All managed Kubernetes |
| Pod Security Admission | Built-in | Low | Kubernetes 1.23+ |
| Custom Webhooks | Both | High | Any Kubernetes |
Pick the solution that best aligns with your team’s skillset and compliance requirements. For most organizations, Kyverno provides the best balance of capability and ease of use — especially for teams new to policy-as-code approaches.
Operational Considerations for Production
Admission controllers become critical infrastructure — so their availability directly impacts cluster operations. Implement these reliability practices:
- Set appropriate timeout values for webhooks (default 10s may be too long)
- Implement failure policy: “Fail” for security controls, “Ignore” for convenience mutations
- Monitor admission webhook latency metrics (histogram_apiserver_admission_step_duration_seconds)
- Ensure webhooks have adequate replica counts and pod disruption budgets
Without these operational guardrails, you might create availability issues while trying to improve security — the exact opposite of DevSecOps principles.
Next Steps: Implementing Your Admission Controls
Start with these actionable steps:
- Audit current cluster state — Use kube-bench or kubectl to check which admission controllers are enabled
- Enable Pod Security Admission — The lowest-effort, highest-value starting point
- Deploy OPA Gatekeeper or Kyverno — Begin in audit mode to measure policy violations
- Create initial policy set — Focus on privileged containers, image sources, and resource limits
- Gradually enforce policies — Move from audit to warn to enforce over 2-3 sprint cycles
Embed these controls early in your development process rather than attempting to retrofit security later when misconfigurations have already proliferated.
FAQ Section
What happens if admission controllers fail?
Kubernetes provides failure policy options: “Fail” (block requests) or “Ignore” (bypass the webhook). For security-focused admission controllers, use “Fail” to ensure secure-by-default operations. Always monitor webhook availability to prevent production issues.
Can admission controllers impact cluster performance?
Yes — poorly designed admission webhooks can increase API latency. Therefore, implement efficient logic, set appropriate timeouts, and monitor performance metrics. In practice, well-optimized admission controllers add minimal latency (typically <100ms per request).
How do admission controllers differ from RBAC?
RBAC controls who can perform actions, while admission controllers control what actions can be performed and how resources should be configured. They provide complementary security layers — so you need both for comprehensive protection.
Are admission controllers available in managed Kubernetes services?
Yes — AWS EKS, Azure AKS, and Google GKE all support admission controllers. Some services even provide managed policy solutions like Azure Policy for AKS or GKE Policy Automation. Check your provider’s documentation for specific implementation details.
What’s the difference between built-in and dynamic admission controllers?
Built-in admission controllers are compiled into the kube-apiserver binary, while dynamic admission controllers (webhooks) run as separate processes and can be updated without modifying the API server. Most modern implementations use dynamic webhooks for flexibility.
No post found!