Network Security: The Definitive Framework for Cyber Resilience in 2025
In the architecture of modern business, the network is the central nervous system. It carries the lifeblood of data that powers operations, enables communication, and drives innovation. This critical role also makes it a primary target for malicious actors. Network security is no longer about simply building a fortified perimeter; it is about constructing an intelligent, adaptive, and resilient defense-in-depth strategy that can operate in a world of encrypted traffic, cloud sprawl, and remote work.
This guide moves beyond basic definitions to provide a comprehensive framework for understanding and implementing enterprise-grade network security. We will dissect the core principles, modern technologies, and strategic implementation steps necessary to protect your organization’s most critical asset: its connectivity.
Target Keywords: network security, cybersecurity network, enterprise network security, network protection, cyber network defense
What is Network Security? Beyond the Firewall
Network security is the comprehensive practice of protecting a computer network infrastructure from unauthorized access, misuse, malfunction, modification, destruction, or improper disclosure. The ultimate goal is to create a secure platform for devices, users, and applications to perform their permitted functions within a secure environment.
It is a critical subset of the broader cybersecurity network ecosystem, acting as the first line of defense against external threats and a crucial control for internal threat mitigation. A mature network security posture is built on three foundational principles, often called the CIA Triad:
- Confidentiality: Ensuring that data is accessible only to those authorized to view it. This is primarily achieved through encryption.
- Integrity: Safeguarding the accuracy and completeness of data and IT systems. This involves protecting data from being altered by unauthorized parties.
- Availability: Ensuring that systems, data, and network resources are accessible to authorized users when needed, protecting against disruptions like Denial-of-Service (DoS) attacks.
The Evolving Challenge: Why Traditional Security is Obsolete
The classic “castle-and-moat” approach—a strong firewall at the network edge—is ineffective today. Key drivers of this change include:
- The Perimeter is Everywhere: With remote work, BYOD (Bring Your Own Device), and cloud applications, the corporate network boundary has dissolved.
- Encrypted Traffic Dominance: While essential for privacy, encryption (TLS 1.3) also blinds traditional security tools, allowing threats to hide in plain sight.
- Sophisticated Threats: Advanced Persistent Threats (APTs) and polymorphic malware are designed to evade signature-based detection.
- Cloud and Hybrid Environments: Data and applications are no longer solely in a corporate data center, requiring security that extends into public clouds.
A modern cybersecurity network strategy must address these challenges head-on.
The Core Components of a Defense-in-Depth Strategy
A robust network security architecture employs a layered approach (defense-in-depth), ensuring that if one control fails, others will still provide protection.
1. Access Control & Perimeter Security
- Next-Generation Firewalls (NGFWs): These are the evolved sentinels. Unlike traditional firewalls that only inspect ports and IP addresses, NGFWs incorporate Deep Packet Inspection (DPI), intrusion prevention systems (IPS), and application-level awareness to identify and block sophisticated threats.
- Network Access Control (NAC): NAC solutions enforce security policies on devices seeking to access the network. They verify device health (e.g., updated antivirus, OS patches) and can segment devices based on identity and type (corporate, guest, IoT), a critical control for IoT security.
2. Threat Prevention & Intrusion Defense
- Intrusion Prevention/Detection Systems (IPS/IDS): An IDS monitors network traffic for suspicious activity and generates alerts. An IPS sits inline and can actively block or drop malicious packets in real-time. Modern solutions are often integrated into NGFWs.
- Advanced Malware Protection (AMP) & Sandboxing: These tools analyze files and code in a safe, isolated environment (a sandbox) to detect zero-day and evasive malware before it enters the network.
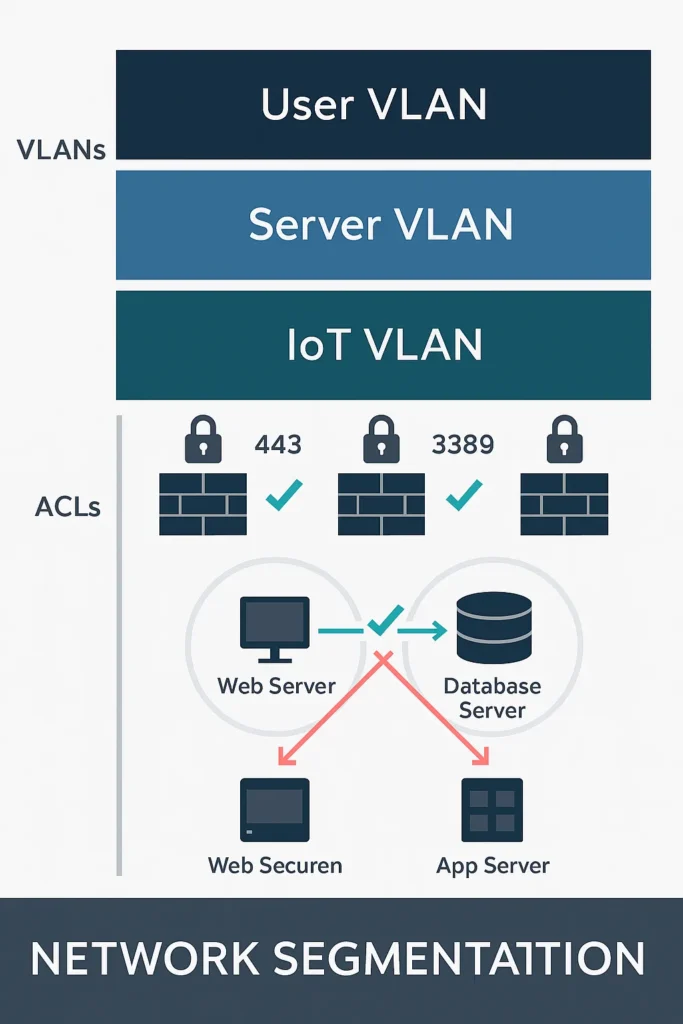
- Network Segmentation: The practice of dividing a network into smaller, isolated subnetworks (segments or zones). This limits an attacker’s ability to move laterally across the network after a breach. Micro-segmentation takes this to the individual workload level.
3. Secure Connectivity & Privacy
- Virtual Private Networks (VPNs): Provide secure, encrypted tunnels for remote users to access the corporate network over the public internet. While still prevalent, they are being supplemented by more granular Zero Trust models.
- Secure Web Gateways (SWG): Protect users from web-based threats by filtering unwanted software/malware from user internet traffic and enforcing corporate and regulatory policy compliance. They often include URL filtering, data loss prevention (DLP), and antivirus scanning.
- Email Security Gateways: The first line of defense against phishing, malware, and business email compromise (BEC) attacks, which often target the network through its users.
4. Visibility, Analysis, and Response
- Network Detection and Response (NDR): A critical category of tools that use behavioral analytics and machine learning to analyze network traffic patterns (east-west and north-south) to detect anomalous activity that indicates a threat, such as lateral movement or data exfiltration. This is essential for finding threats that bypass other controls.
- Network Traffic Analysis (NTA): The process of collecting and analyzing network traffic data to improve performance and identify security threats.
Implementing a Zero Trust Architecture for Network Security
The modern answer to the dissolved perimeter is Zero Trust. The mantra is “Never trust, always verify.”
A Zero Trust cybersecurity network model assumes that no user or device, inside or outside the network, should be trusted by default. Access is granted on a per-session basis after strict identity verification. Key components include:
- Identity and Access Management (IAM): Strong multi-factor authentication (MFA) is the cornerstone.
- Software-Defined Perimeter (SDP): Technology that hides critical infrastructure from the public internet, only allowing connections from authorized and authenticated users.
- Micro-segmentation: As mentioned, this is a core enabling technology for Zero Trust, preventing lateral movement.
Building Your Network Security Roadmap: A 5-Step Plan
- Assess & Map: Conduct a thorough audit of your current network architecture, assets, data flows, and existing security controls. Identify critical vulnerabilities and gaps.
- Define Policy: Establish clear, enforceable security policies for access control, acceptable use, and incident response. This policy must be endorsed from the top down.
- Prioritize Implementation: Focus on quick wins with high impact. This often means:
- Enforcing MFA everywhere.
- Patching critical vulnerabilities.
- Implementing core segmentation to isolate sensitive data.
- Deploy Advanced Tools: Invest in technologies that provide visibility and control, such as NGFWs, NDR, and a robust NAC solution.
- Monitor, Test, and Adapt: Continuously monitor your network with NDR and SIEM tools. Conduct regular penetration testing and red team exercises to validate your defenses and adapt to the evolving threat landscape.
Network security is not a product you buy; it is a continuous process of adaptation and vigilance. By understanding these principles and implementing a layered, intelligent strategy centered on Zero Trust, your organization can build a resilient cybersecurity network capable of withstanding the threats of today and tomorrow.
Related Topics & Deep Dives
To further your knowledge on enterprise network security, explore our detailed guides on:
Securing IoT Devices in an Enterprise Network:
Implementing Zero Trust: A Practical Guide for Network Architects: A step-by-step playbook for moving to a Zero Trust model.
Next-Generation Firewall (NGFW) Buyer’s Guide: Features & Comparisons: How to evaluate and select the right NGFW for your enterprise.
The Ultimate Guide to Network Segmentation: Strategies for planning and implementing segmentation to contain breaches.
NDR vs. NGFW: Understanding the Differences and Synergies: How these technologies work together for superior threat detection.
Securing IoT Devices in an Enterprise Network: Specific strategies for managing the risk posed by the proliferation of Internet of Things devices.
No post found!
Frequently Asked Questions About Network Security
1. What is network security in simple terms?
Network security is the practice of protecting a company’s network and data from unauthorized access, misuse, or attacks. It ensures confidentiality, integrity, and availability — often called the CIA Triad.
2. Why is the traditional firewall approach no longer enough?
Modern networks span cloud, remote work, and IoT. A single perimeter defense can’t protect against encrypted threats, lateral movement, or hybrid architectures. Organizations need layered, adaptive defenses.
3. What are the core components of a defense-in-depth network security strategy?
Key layers include next-generation firewalls (NGFWs), intrusion prevention and detection (IPS/IDS), network segmentation, secure connectivity (VPNs, SWGs, email gateways), and advanced monitoring like NDR.
4. How does Zero Trust improve network security?
Zero Trust assumes no user or device is trustworthy by default. It enforces strict verification, uses micro-segmentation, and applies least-privilege access. This reduces the risk of lateral movement and insider threats.
5. What role does network segmentation play in cyber resilience?
Segmentation limits attacker movement within the network. Even if one area is breached, sensitive systems remain isolated. Micro-segmentation goes further by securing workloads individually.
6. What tools are critical for detecting advanced network threats?
Network Detection and Response (NDR), Network Traffic Analysis (NTA), and advanced malware sandboxing are essential. They provide visibility into encrypted traffic and help identify anomalies that bypass traditional defenses.
7. How should enterprises start building a network security roadmap?
Begin with an assessment of assets and vulnerabilities, define security policies, enforce MFA and patching, implement segmentation, then deploy advanced tools like NDR and NGFW. Continuous monitoring and testing complete the cycle.
The Ultimate Guide to VPNs
The Ultimate Guide to VPNs: Protocols, Security Myths, and Enterprise Deployment You’ve probably heard of…
The Ultimate Guide to Firewalls: From Basics to Next-Gen Policies
The Ultimate Guide to Firewalls: From Basics to Next-Gen Policies Let’s be honest. “Firewall” is…
Segmentation
Network Segmentation & Microsegmentation: The Ultimate Guide to Stopping Lateral Movement In the world of…
VPN Security
VPN Security: Building a Secure Tunnel, Not a Vulnerable Gateway The Virtual Private Network (VPN)…
Firewalls Basics
Firewalls 101: The Definitive Guide to Network Security’s First Line of Defense In the architecture…
Zero Trust Networking: Principles & Implementation
Zero Trust Networking: Beyond the Castle-and-Moat Model The traditional network security model has long operated…
DDoS Defense
DDoS Defense: Modern Strategies & Essential Tools to Protect Your Network DDoS Defense A Distributed…
IDS vs IPS
IDS vs. IPS: Your Guide to Network Detection and Prevention In the relentless battle to…
Next-Gen Firewalls Explained: Policies, TLS Inspection, and Best Practices
If you can’t see it, you can’t secure it. Next-Generation Firewalls (NGFWs) are the cornerstone…
Network Segmentation Guide: VLANs, ACLs, and Microsegmentation
If you can’t see it, you can’t secure it. Flat networks are a legacy risk…