Every minute an advanced threat hides in your network, the potential for data breach and operational downtime grows. Ad-hoc queries are a start, but they are the digital equivalent of a fire drill without a plan. A mature threat hunting program transforms this reactive effort into a disciplined, proactive security operation. In this guide, I’ll walk you through building a program that moves beyond one-off searches to sustained, intelligent threat discovery.
Why Ad-Hoc Queries Aren’t Enough for Modern Defense
Many teams begin their hunting journey with ad-hoc searches — a compromised credential alert leads to a query for unusual logon times. This is valuable, but it’s not hunting. This approach is reactive, relies on luck, and its findings are difficult to scale or replicate.
A formal program provides the safety net your organization needs. It shifts your focus from singular Indicators of Compromise (IOCs) to understanding adversary TTPs (Tactics, Techniques, and Procedures). This proactive stance is critical for finding persistence mechanisms and C2 (Command and Control) channels that automated tools miss. The business impact is clear: reduced dwell time, lower downtime cost, and preserved customer trust.
The Core Components of a Threat Hunting Framework
Building a threat hunting program requires more than just tools; it requires a methodology. Think of it as building a playbook for your most skilled analysts.
- People & Skills: You need hunters with deep curiosity and analytical skills, trained in digital forensics and network analysis. Start with your top SOC tier 2/3 analysts.
- Process & Methodology: This is the engine of your program. The most effective model is a hypothesis-driven approach:
- Hypothesis: “An APT group targeting our sector may use DNS tunneling for data exfiltration.”
- Investigation: Query and analyze DNS logs for anomalies (e.g., long domain names, high frequency requests to new domains).
- Uncover & Triage: Identify potential malicious activity and assess its scope.
- Inform & Enhance: Document the TTPs and create new alerts for your SOC to automate detection in the future.
- Technology & Data: You cannot hunt without evidence. Ensure you have the right data with appropriate retention periods: endpoint logs (EDR), network flow data (NetFlow), DNS query logs, and authentication events. Centralize this in a SIEM or data lake.
A Step-by-Step Playbook to Launch Your Program
Start with containment of scope, then move to execution. Don’t try to boil the ocean in your first quarter.
Phase 1: Foundation (Months 1-2)
- Secure executive sponsorship by translating hunting goals into regulatory impact and risk reduction.
- Assemble a core team of two hunters and define a weekly hunting cadence.
- Conduct a data gap analysis — can you access the logs you need for common hypotheses?
Phase 2: Operationalization (Quarter 1-2)
- Run your first hypothesis-based hunt based on a recent threat intelligence report relevant to your industry.
- Focus on a single hypothesis per session. Depth beats breadth in hunting.
- Document findings as you go — this is non-negotiable for building institutional knowledge and refining your process.
Phase 3: Maturation (Quarter 3+)
- Formalize a process for converting successful hunts into new SIEM alerts and SOC playbooks. This is how you demonstrate ROI.
- Start measuring success through metrics: hypotheses investigated, true positives confirmed, and mean time to detection (MTTD) reduction.
From Theory to Practice: A Real-World Hunting Hypothesis
Let’s apply the framework. Suppose intelligence suggests a rise in ransomware groups using living-off-the-land techniques.
- Hypothesis: “Threat actors may be using native Windows utilities like WMI or PowerShell for lateral movement and execution, evading traditional AV.”
- Investigation: Hunt for WMI and PowerShell executions that originate from unexpected source IPs or users, especially outside business hours.
- Key Finding: You discover a series of WMI events from a user’s workstation initiating connections to a database server. This was missed by alerts.
- Lesson Learned: The hunt uncovered a TTP. You then create a new correlation rule in your SIEM to alert on WMI executions from workstations to critical servers, effectively closing the detection gap.
Always close with validation: Ensure your new alert is tuned to reduce false positives and that your SOC team is trained on its response.
FAQ: Threat Hunting Programs
Q: How is threat hunting different from what my SOC does today?
A: Your SOC operates a factory of automated alerts — it’s reactive. Threat hunting is a dedicated, human-driven process to proactively search for evidence of evil that your automated tools have not yet been programmed to find. The SOC responds to alerts; hunters find what the alerts missed.
Q: Do I need expensive new tools to start threat hunting?
A: No. Start with the data you have. The most important tool is a curious analyst and a capable SIEM or data platform. While specialized EDR and network analysis tools are powerful force multipliers, you can begin hunting with well-structured log data. Skipping imaging saves time but destroys evidence integrity — never cut this corner on data collection.
Q: How do we measure the success and ROI of a threat hunting program?
A: Avoid vanity metrics. Focus on leading indicators like the number of confirmed threats discovered that were previously unknown, and lagging indicators like the reduction in dwell time (the time a threat is present before detection). The ultimate ROI is a new automated detection that prevents a future incident.
Q: We’re a small team. Can we realistically do this?
A: Absolutely. Start small. Dedicate one analyst 20% of their time to formal, hypothesis-driven hunting. This is far more valuable than having everyone run ad-hoc queries. The key is consistency and documentation, not the size of the team.
Ready to move beyond ad-hoc? The best next step is to run a tabletop exercise this quarter focused on a specific adversary TTP. Gather your team, define a hypothesis, and walk through the data you would need to investigate it. This practice will reveal gaps and build momentum for a formal program.
Share how your team built its hunting capability on our LinkedIn page. What was your first successful hypothesis?
Healthcare Ransomware Case Study 2025
Anatomy, Impact & NIST CSF DefenseCase Study: Responding to a Healthcare Ransomware Attack Introduction: When…
Service Mesh vs API Gateway: Security Implications
Security should move at the speed of your pipeline. As organizations modernize with Kubernetes and…
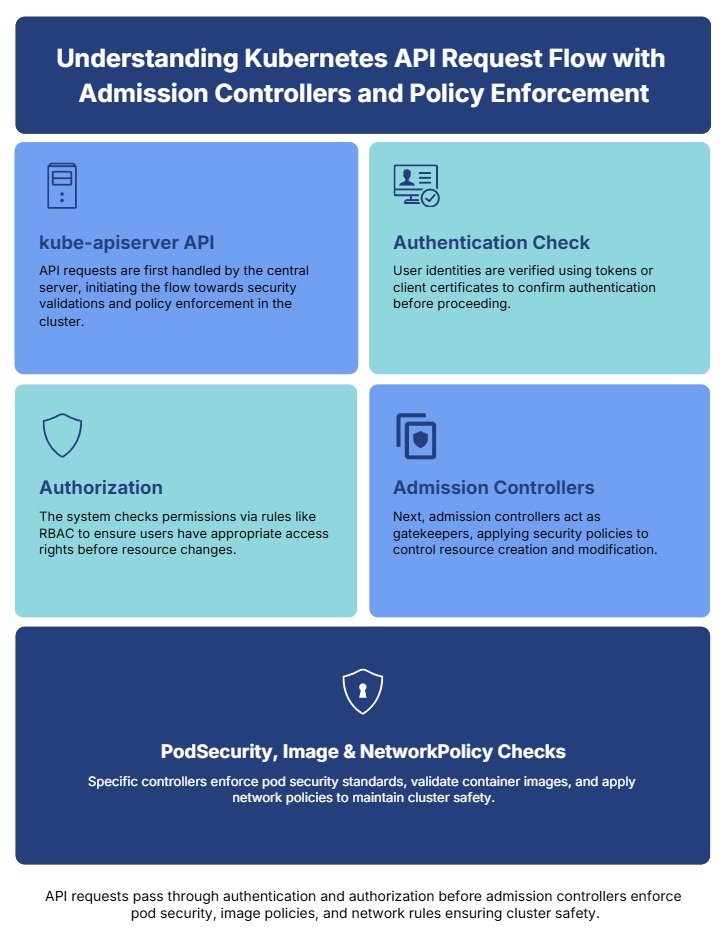
Kubernetes Admission Controllers: Security Use Cases – Complete Guide
Security should move at the speed of your pipeline. When teams scale to multiple clusters,…
Container Supply Chain Security: Image Signing and Verification
In the modern CI/CD pipeline, the container is the new currency of deployment. But just…
Serverless Functions Security: AWS Lambda, Azure Functions, GCP Cloud Functions
Securing Serverless Functions Security should move at the speed of your pipeline. Serverless computing accelerates…
Multi-Tenant Kubernetes Security Challenges
When teams scale to multiple clusters, visibility gaps grow fast. Kubernetes was designed for flexible…